INSTALLING & ACCESSING BACKDOOR
INTRODUCTION
- Metasploit has a ability to install a backdoor on remote pc to maintain access after the exploitation .
- Through the metsvc module , you can create a persistant backdoor on a remote PC .
THINGS TO REMEMBER
- The ' metsvc ' service require no authentication , it means if anyone find our backdoor they can also access it .
INSTALLING BACKDOOR
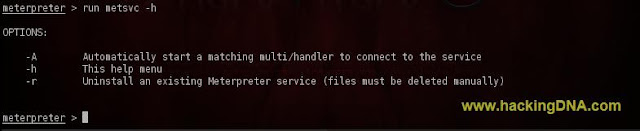
HELP COMMAND
- Command Used : run metsvc -h
- This command will show you the options .
RUN METSVC(Installing Backdoor)
- To install backdoor use the command .
- Command Used : run metsvc
- In the below image you can see the files are uploading on the remote system .
- See the below image for more details -
HERE IS THE BACKDOOR INSTALLED
- In the below image you can see the folder named rNuqIiQCSiN is successfully uploaded in the Temp directory of Remote PC .
- See the below image for more details -
Inside the Directory
- Here you can see the metsrv dll and exe files .
- See the below image for more details -
RESTART MY WINDOWS XP
- After setting the backdoor successfully on the remote system , now I am going to restart remote PC .
- The reason behind the restarting is to check ,wheater the backdoor i have installed will worked or not.
- See the below image , it show my remote pc ( Windows xp ) is starting -
ACCESSING BACKDOOR
- Now time to Accessing the Backdoor that we created .
- To access the Remote PC again. We have to use the multi_handler with Payload .
- See all the steps below to access the backdoor , that we set before -
Step 1 : Set Multi handler Exploit
- See the below image for the comamnd -
Step 2 : Set PAYLOAD
- See the below image for the command -
Step 3 : Checking all Fields
- To checking all the fields , use the show options command .
- See the below image for the command .
Step 4 : Set RHOST & LPORT
- In this step you have to Set the Remote Host & Local Port .
- See the below image for more details -
Step 5 : Last Checking
- In this step for the last time check it again all the fields .
- To check we again use the show option again .
- See the below image for more details -
Step 6 : Exploit ( FINAL STEP )
- Now this is the Final Step , you just have to exploit the target to get the meterpreter session again .
- Enter the Command : exploit and hit enter .
- And finally we get the meterpreter session again .
On Windows (Task Manager)
- On Windows Task Manager , you can see the meterpreter-server.exe process is running on your SYSTEM .
- See the below image for more details -
AT THE END
- Q. Why we use port 31337 ?
- A. Because port is used for all the backdoor services . So if you use different ports it will not create a meterpreter session when you exploit .
- So remember to use the port 31337 .
- Also 31337 is a hackerz spelling of 'elite', meaning 'elite hackers'.
I hope you like this tutorial . Any feedback are warm welcome .












No comments:
Post a Comment