Honeypot
Introduction
- Using Pentbox ,we are going to create a small honeypot . (just for educational purpose only ).
- We set the honeypot on backtrack 5 .
- Firstly you have to download Pentbox on you backtrack 5 , if it is not install on your backtrack 5 .
- You can see our Pentbox tutorial to learn how to install Pentbox on Backtrack 5 .
- link - http://www.hackingdna.com/2012/03/learn-pentbox-on-backtrack-5.html
- Once you install the Pentbox , now run it .
- See the below image your Pentbox shows some options-
NETWORK TOOLS
- To select network tools you have to enter number : 2
- See the below image for more details -
HONEYPOT
- After pressing enter key network tools options will display , now you have to select the Honeypot options .
- To select honey , enter number 3 and press enter key .
- See the below image for more details -
// Honeypot Setting //
- Now select the 2nd option ( Manual Configuration ).
- Enter number : 2 and press enter key
Insert Port number
- Insert the port number , here in my case i have enter port 23 .
- See the below image for more details -
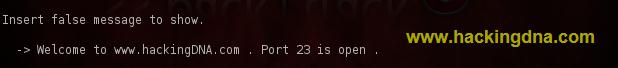
Insert false message
- Now insert the false Message , i have entered ( Show in the below image ) .
- You can type any message . Which is display on the attacker machine when they try to connect port 23 .
- See the below image for more detials -
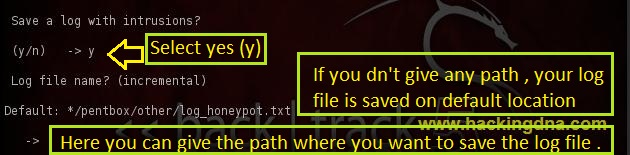
Save a log
- To save all the intrusions in a log file , you have to enter y(yes) option .
- Next , it will display the default path of log file , this option will activated if you don't give any manual path .
- See the below image for more details -
Activate Beep sound
- If you activated Beep sound , then whenwver a intrusion takes place a beep sound will alert you .
- To activate beep sound , insert y (yes) and press enter key .
- See the below image for more details -
ATTACKER SYSTEM
- Suppose this is a attacker system ( metasploitable ) .
- When attacker is try to connect to port 23 , he got the fake message which we enter at the time of manual configuration .
- See the below image for more details -
- Below on the Backtrack 5 machine , some intrusion detected from 192.168.232.129.
- So now we can say our honeypot is working successfully .
- See the below image for more details -
LOGFILE
- Now let see the log file , is it filled with intrusions or not .
- To open log file , go to its default location as shown below -
- See the below image for help -
This is how we can use this small honeypot on backtrack 5
If you like it and wanna need more updates










No comments:
Post a Comment