Introduction
- Nmap ("Network Mapper") is an open source tool for network exploration and security auditing.
- It was designed to rapidly scan large networks, although it works fine against single hosts.
- Nmap uses raw IP packets in novel ways to determine what
- hosts are available on the network,
- what services (application name and version) those hosts are offering,
- what operating systems (and OS versions) they are running,
- what type of packet filters/firewalls are in use, and dozens of other characteristics.
- While Nmap is commonly used for security audits,
- Many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
HOW TO OPEN NMAP
- BackTrack > Information Gathering > Network Analysis > Network Scanners > nmap
- When you open nmap in backtrack 5r2 , it look like the below image -
USAGE
Usage:nmap[Scan Type(s)][Options]{targetspecification}
For Help :
- For help you can use 2 commands -
- Command 1 : nmap -h
- Command 2 : man nmap
HOST DISCOVERY SCANNING
EXAMPLE 1 : LIST SCAN
- -sL: List Scan - simply list targets to scan.
- See the below example of list scan ( -sL )
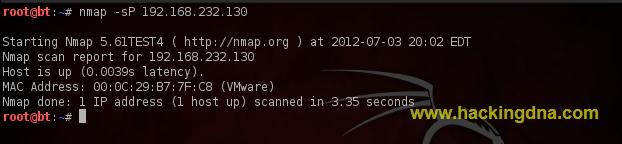
EXAMPLE 2 : PING SCAN OR PING SWEEP SCAN- -sP: Ping Scan - go no further than determining if host is online .
- See the below image for more help-
EXAMPLE 3 : -PN: - Treat all hosts as online -- skip host discovery .
- See the below image -
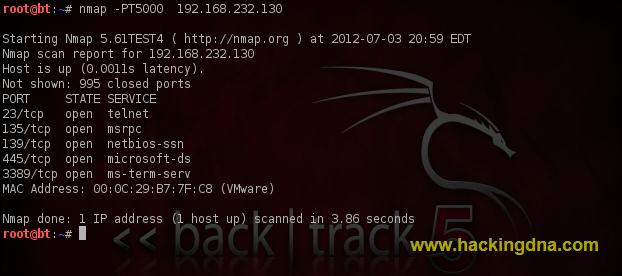
EXAMPLE 4 : TCP PINGING- Using -PT flag , we perform Tcp Pinging Scan .
- See the below image for more details -
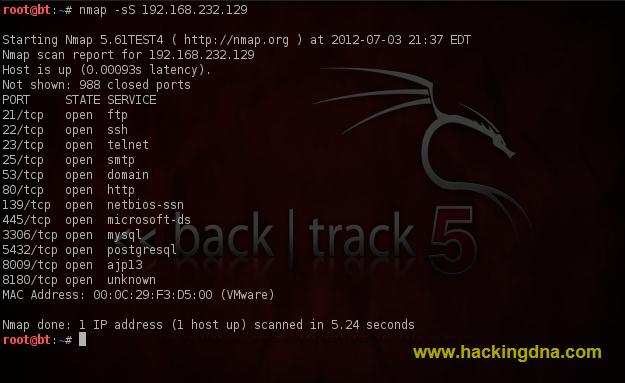
SCANNING TECHNIQUESEXAMPLE 5 : tcp SYN Scan - Using -sS flag in nmap we perform the SYN scan .
- See the below image for help -
EXAMPLE 7 : TCP Connect Scan- Using -sT flag , we will perform TCP Connect Scan .
- See the below image for more details -
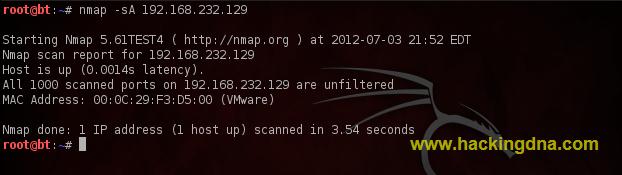
EXAMPLE 8 :TCP ACK SCAN- Using -sA flag ,we can perform a Ack (Acknowledgement ) Scan.
- See the below image for ACK Example -
EXAMPLE 9 :TCP WINDOW SCAN- Using -sW flag , we can perform a Tcp Window Scan .
- See the below image for more details -
EXAMPLE 10 : TCP Maimon Scan- Using -sM flag , we will perform Maimon Scan in Backtrack 5 .
- See the below image for more details -
EXAMPLE 11 : Null Scan- Using -sN flag , we perform NULL Scan .
- See the below image for NULL Scan example -
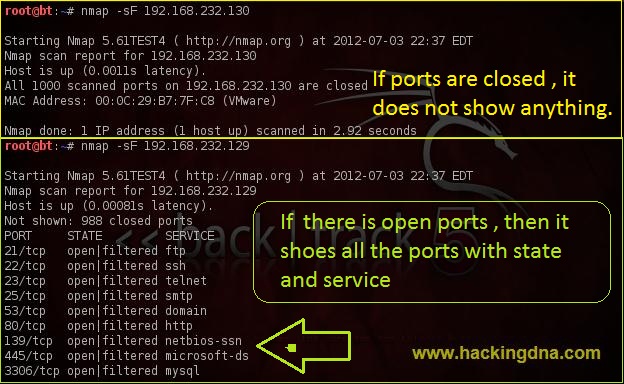
EXAMPLE 12: FIN SCAN- Using -sF flag, we perform FIN( FINISH ) Scan .
- See the below image for more details -
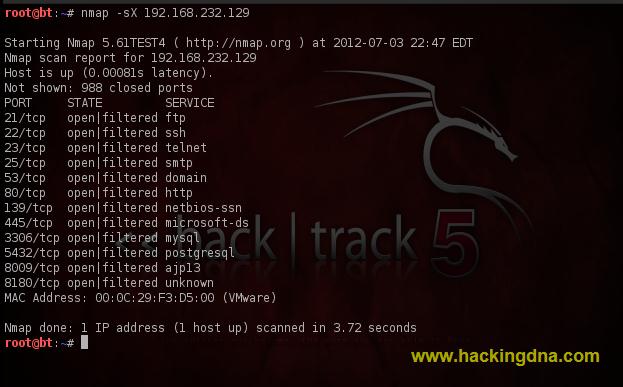
EXAMPLE 13 : XMAS SCAN- Using -sX flag , we perform XMAS Scan .
- See the below image for more details -
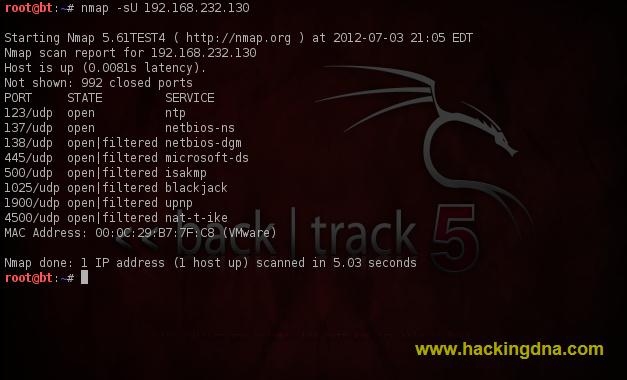
EXAMPLE 14:UDP SCAN - Using -sU flag , we perform UDP Scan .
- See the below image for more details -
EXAMPLE 15 : - Enable OS Detection , version detection , scriptdetection and traceroute .
- Command used : nmap -A < Target ip addres >
- Here we use -A flag .
- See the below image for more details -
Lots of other example will be updated soon . Thanks for watching !












No comments:
Post a Comment