Introduction
- DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux Command Line program coded purely in C with the ability to gather as much information as possible about a host.
- DMitry( ( Deepmagic Information Gathering Tool ) is created by James Greig .
How To Open DMitry
- To open DMitry goto , BackTrack > Information Gathering > Network Analysis > Route Analysis > dmitry
- See the below image for more details -
HELP OPTION
- To use help option , enter the command given below .
- Command Used : dmitry -h
- See the below image for more details -
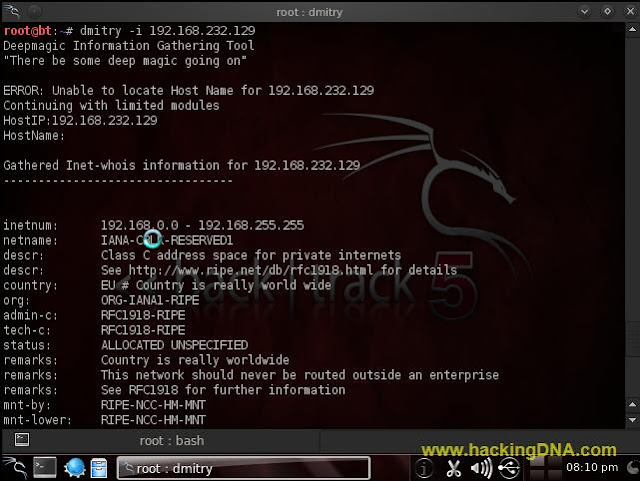
-i Option
- Perform an Internet Number whois lookup on the target. This requires that the target be in the form of a 4 part Internet Number with each octal seperated using the '.' notation. For example, "dmitry -i 255.255.255.255".
- See the below image for more details -
-w Option
- Perform a whois lookup on the 'host' target. This requires that the target be in a named character format. For example, "./dmitry -w target" will perform a standard named whois lookup.
- See the below image for moe details -
-n Options
- Retrieve netcraft.com data concerning the host, this includes Operating System, Web Server release and UpTime information where available.
- See the below image for more details -
-s Option
- Perform a SubDomain search on the specified target.
- This will use serveral search engines to attempt to locate sub-domains in the form of sub.target.
- There is no set limit to the level of sub-domain that can be located, however, there is a maximum string length of 40 characters (NCOL 40) to limit memory usage.
- Possible subdomains are then reversed to an IP address, if this comes back positive then the resulting subdomain is listed.
- However, if the host uses an asterisk in their DNS records all resolve subdomains will come back positive.
- See the below image for more details -
-e Option
-p Option
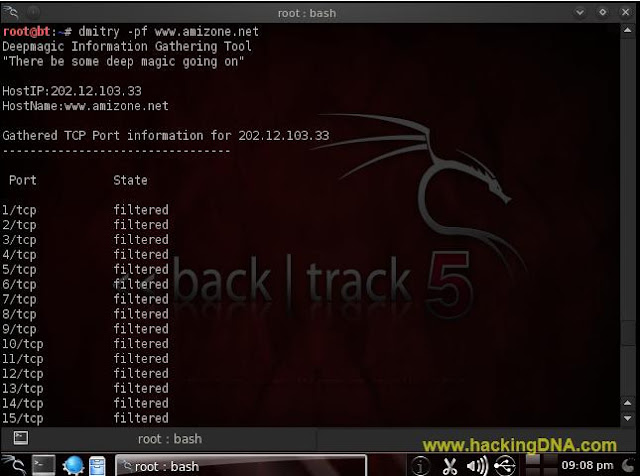
-f option
- This option will cause the TCP Portscan module to report/display output of filtered ports. These are usually ports that have been filtered and/or closed by a firewall at the specified host/target. This option requires that the '-p' option be passed as a previous option. For example, "dmitry -pf target".
- See the below image for more details -
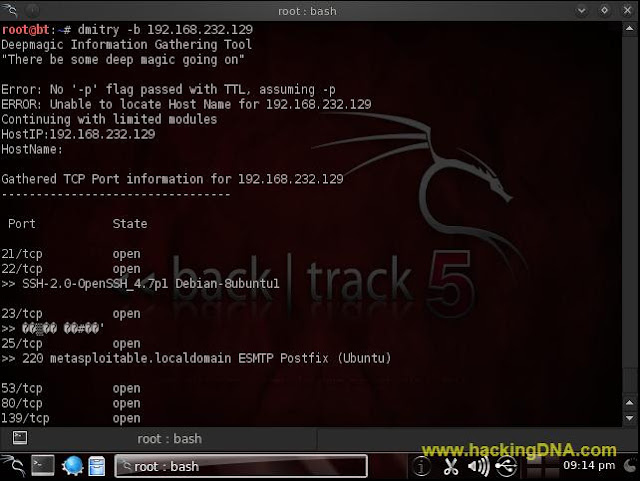
-b Options
- This option will cause the TCP Portscan module to output Banners if they are received when scanning TCP Ports. This option requres that the '-p' option be passed as a previous option.
- See the below image for more details -
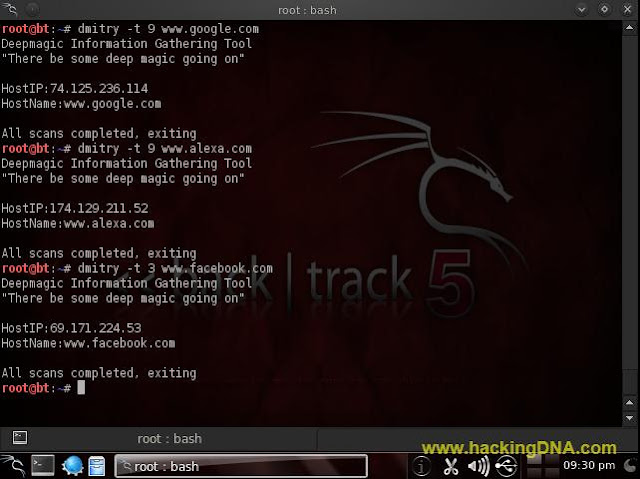
-t option
- This sets the Time To Live (TTL) of the Portscan module when scanning individual ports. This is set to 2 seconds by default. This is usually required when scanning a host that has a firewall and/or has filtered ports which can slow a scan down.
- See the below image for more details-
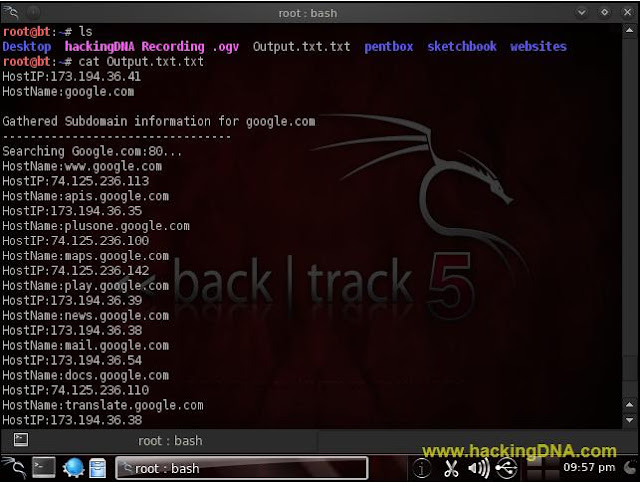
-o Option
- Create an ascii text output of the results to the "filename" specified.
- If this option is not specified in any form output will be sent to the standard output (STDOUT) by default.
- See the below image for more details -
THIS IS HOW WE CAN USE " DMitry Tool " ON BACKTRACK 5












No comments:
Post a Comment